08 9228 2945

IT security penetration testing, also known as “PEN Testing” is a process used to test the defences of an IT system. PEN tests play a key role in maintaining and better securing your IP, network, physical, cloud or even the less tangible social and cultural aspects of your cyber security.
More recently, many Australian companies have been exposed to social and cultural security vulnerabilities. Our team can help develop your company’s culture to ensure that while technology is still crucial, cyber security is now the responsibility of everyone playing their role. Through policy, process, role definition, training and awareness, Epic IT can help your organisation make this change.
During a PEN test, our cyber security team is granted permission by the customer to ethically hack, test and identify potential vulnerabilities within their IT system. The team will document the entire testing process and provide the customer with a detailed security report. This information is then used to further protect the IT system from threats that were uncovered during the test.
Our cyber security team is available to help mitigate these threats. If the customer is not a managed (MSA) partner, we can work with the existing IT professionals of the customer to implement the recommendations of the report.
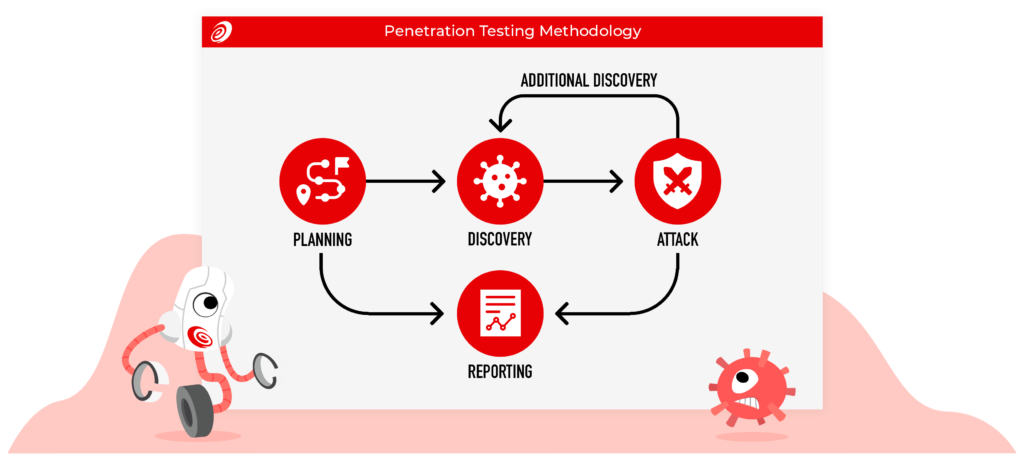
Below we break down the key benefits of conducting either one off or recurring pentetration testing programs.
Getting started is easy. Identify your key cyber security goals and call our team today on 08 9228 2945. we will do the rest.
Have a chat to our team on .. 08 9228 2945
Like to learn more about our services?
Please let us know what you are chasing and we will respond same day.